HIPAA Compliance & Security
Is video conferencing HIPAA compliant?
OrthoLive helps you to be HIPAA compliant in two ways:
- It protects data privacy in that all audio/video communication is securely encrypted and transmitted from point-to-point such that even OrthoLive and other technology partners does not have access to any identifiable health information that may be communicated.
- OrthoLive offers the HIPAA-required Business Associate Agreement where OrthoLive agrees to be responsible for keeping all patient information secure and to immediately report any breach of personal health information.
What You Need To Know About HIPAA
HIPAA and Health IT
HIPAA is a federal law that protects the privacy of your personal health information. At the same time, it allows health care providers and certain related operations enough access to the information they need to do their jobs effectively. HIPAA includes several rules and provisions that set guidelines and requirements for the administration and enforcement of HIPAA.
The relevant ones for the implementation of health information technology and the exchange of protected health information in an electronic environment are the Privacy Rule and the Security Rule, as well as the HITECH Act which further enforced the two in 2009.
*State laws may have more stringent requirements than federal laws, however, in cases of conflict, federal law supersedes state law.
Highlights Of The Privacy Rule, The Security Rule, and the HITECH Act
- The Privacy Rule, applies to protected health information (PHI) in any form whether paper, oral, electronic, etc. While it requires covered entities to put in place “administrative, physical, and technical safeguards” for protecting PHI, it differs from the Security Rule in that it discusses the cases in which PHI can be used, when authorization is required and what are patients’ rights with respect to their health information. (Page 8335 of the final Security Rule)Summary of Privacy Rule
- The Security Rule applies only to protected health information in electronic form (E-PHI) and builds on the Privacy Rule requirements of “administrative, physical, and technical safeguards.” Unlike the Privacy Rule which is more concerned about patients’ rights and how health information is used and released, the Security Rule sets standards on the processes and technical security measures that should be taken to keep PHI private. It discusses acceptable ways to “implement basic safeguards to protect E-PHI from unauthorized access, alteration, deletion, and transmission.” (Page 8335 of the final Security Rule)* Under the Security Rule, paper to-paper faxes, person-to-person telephone calls, video teleconferencing, or messages left on voice-mail do not count as E-PHI because they did not exist in electronic form before the transmission. Thus those activities are not covered by [the Security Rule]” (Page 8342 of the final Security Rule). In contrast, the Privacy Rule applies to all forms of PHI.In particular, it calls for attention to
- risk analysis and management
- administrative, technical, and physical safeguards
- organizational requirements
- policies, procedures, and documentation requirements
The Security Rule 101 Overview
Security Rule Guidance Material
The US Department of Health & Human Services (HHS) now also offers a Security Risk Assessment (SRA) tool to help organizations ensure they are compliant with HIPAA’s administrative, technical, and physical safeguards and to expose areas where their PHI may be at risk
The figure below gives you an idea of the security measures covered by the Security Rule. (from paper “Reassessing Your Security Practices in a Health IT Environment: A Guide for Small Health Care Practices”)
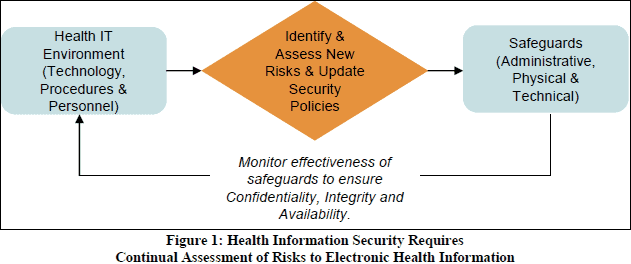
- The HITECH Act essentially added teeth to the HIPAA Privacy and Security Rules by specifying levels of violations and penalties for violations. It also requires periodic audits to ensure that covered entities and business associates are complying with the HIPAA Privacy and Security Rules and Breach Notification.HITECH modifications to privacy and security
Who Is Required To Comply With HIPAA?
Not all operations that handle health-related information must follow HIPAA law (such as many schools, state agencies, law enforcement agencies, or municipal offices). Under HIPAA the 2 groups that must follow HIPAA rules are
- covered entities – health care providers, health plans, and health clearinghouses
- business associates – a person or group providing certain functions or services for a covered entity which require access to identifiable health information, such as a CPA firm, an attorney, or an independent medical transcriptionist; More business associate FAQs here
OrthoLive would be considered the business associate of a covered entity that uses OrthoLive in communicating private health information with a client.
Is A Software Vendor Considered a Business Associate Under HIPAA?
It depends. If a vendor or subcontractor transmits, maintains, or has routine access to protected health information (PHI) when providing its services to a covered entity then it is considered a business associate. For example, a vendor that hosts the software containing patient information on its own server or accesses patient information when troubleshooting the software, then it is considered a business associate and must have a business associate agreement with the covered entity as specified under the HIPAA Privacy Rule 45 C.F.R. § 164.504(e).
The only exception under HITECH section 13408 is in the case of a data transmission organization that acts as a conduit, in that it only transports information but does not access it, such as the US Postal Service or its electronic equivalent — Internet Service Providers (ISPs), a telecommunication company, etc. While these may have access to PHI, they only access PHI on a random or infrequent basis as necessary for the performance of the transportation service or as required by law: “[D]ata transmission organizations that do not require access to protected health information on a routine basis would not be treated as business associates” (p. 22)
While OrthoLive never has access to any information, health or otherwise, that you may observe, transmit, or receive by using OrthoLive, it is still considered a business associate because it is used to transmit private health information over the Internet. To be HIPAA-compliant, a covered entity using OrthoLive for this purpose must have a Business Associate agreement with OrthoLive.
U.S. Department of Health on Software Vendors
U.S. Department of Health on Conduits
How is HIPAA involved in your use of video conferencing?
Videoconferencing may involve the electronic exchange of health information which is protected under HIPAA law. Security considerations with videoconferencing may involve making sure unauthorized third parties cannot to record or “listen in” on a videoconferencing session, making sure recorded videoconferencing sessions are stored and identified in a secure and proper manner, or having a procedure for initiating and receiving video calls. Other video collaboration features affecting security may include text chat, screen-sharing, and file-transfer.
Videoconferencing would only be one small piece to consider when establishing and maintaining HIPAA-compliant IT security standards as described by the Privacy Rule and the Security Rule.
How does OrthoLive allow you to comply with the HIPAA Privacy and Security Rules?
OrthoLive has several characteristics that make it easy to protect the confidentiality of protected health information:
-
- Peer-to-Peer sessions
OrthoLive uses a managed peer-to-peer architecture, where video (and other media) are streamed directly from endpoint to endpoint. Information is never stored on any OrthoLive servers or intercepted by OrthoLive in any way. The OrthoLive management server is only used for address look up, connection brokering, and system/user administration. This prevents information leakage between point A and point B.
-
- Encryption
Encryption adds another layer of security of OrthoLive. All OrthoLive traffic is encrypted with FIPS 140-2 certified 256 bit Advanced Encryption Standard. No servers, including OrthoLive’s, have access to the decryption keys. This keeps keeps your videoconference absolutely confidential.
-
- Local File Storage (of non-streaming media)
OrthoLive allows users to record videoconferences and keeps chat history that could be regarded as electronic protected health information (e-PHI). These files are stored on a user’s computer and are not accessible to OrthoLive. Covered entities may securely save recorded conferences or chat histories to their own HIPAA compliant electronic health record (EHR) system.
